pen test on thick client|thick client pentest checklist : trading Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and . webCom um design moderno e uma interface intuitiva, a app destina-se a todos clientes particulares Montepio24 e representa acima de tudo conforto e comodidade para que trate do seu dia-a-dia financeiro no conforto do seu iPhone ou iPad. A partir de agora pode trazer o seu banco de sempre no bolso.
{plog:ftitle_list}
17 de set. de 1981 · 《DAS BOOT》直译过来是《船》,这是我迄今为止看到的最长的电影了(《星战6部曲》、《魔戒3部曲》这些系列电影不算),长达4小时53分钟。 《DAS BOOT》首次上映是在1981年9月17日,当时放的版本是3小时36分钟的,1982年在美国放的时候被压缩到2小时29 .
Thick client penetration testing (pentest) involves evaluating the security of such locally run applications to identify vulnerabilities, assess potential risks, and recommend security measures to protect against exploitation or . How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. In Thick Client, there are two types (i) Proxy-based Thick clients. (ii) Non-Proxy based thick . Thick client penetration testing is an assessment process aimed at evaluating the security of these desktop applications by identifying vulnerabilities, testing authentication mechanisms, assessing data encryption, . Looking for Comprehensive Thick Client Pen Testing? Thick client applications often don't get the security attention they need, with focus usually on web and mobile apps. .
Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and .
When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It . As a result, both the request as well as response modifications play a key role in testing the thick client for vulnerabilities. Sample Exploit 1. . GADI007 is an Information Security Professional with experience in network and application penetration testing. He is currently a security researcher at Infosec Institute and works for a .
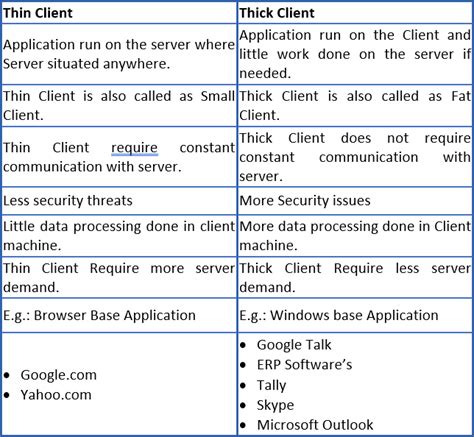
Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities. A thick client application, also known as a fat client , is a software program that runs on a local machine and communicates with a server or a database to perform its .This course introduces students to the penetration testing concepts associated with Thick Client Applications. This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. Thick client penetration testing is a specialized practice that focuses on identifying and addressing security flaws within these locally executed applications. This blog post aims to delve into .Enrol on a thick client penetration testing course to get an insight into the thick client penetration testing methodology. Learn thick client penetration testing tools, thick client enumeration, thick client vulnerabilities, and exploitation.
web penetration testing checklist
Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. Such process often requires specialized tools and custom .Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses. Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile.
Why thick client penetration testing? Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. Thick clients are majorly used across organizations for their internal operations. Let’s explore few more concepts Standalone Thick Clients vs Networked Thick Clients. 1. Standalone Thick Clients: Operate independently of a network. Example: Microsoft Word, Adobe Photoshop. Types of Thick Client. To test a thick client application the most important task is intercepting the requests fired by the application. On the basis of this benchmark, it can be classified as . Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. This phase aims to identify communication protocols and potential entry points for exploitation.
A practical guide to pentesting thick client applications. . Thick Client Application Penetration Testing Course Introduction Course Introduction (1:37) Help and Support Downloadables Introduction and Lab Setup Introduction to Thick Client Applications (4:12) Lab Setup - Part 1 (2:04) Lab Setup - Part 2 (18:44) The Pre-Course Challenge (2:32) .
Thick Client Penetration Testing aims to assess and ensure the secure deployment of thick client or native applications by simulating real-world attacks and analysing potential weaknesses. This comprehensive testing process helps uncover critical vulnerabilities that could be exploited by malicious actors, ensuring that the application’s .
SecureLayer7 begins its thick client application pen testing service by understanding each application's intricacies and functionality. The methodology involves reverse engineering to identify hard-coded secrets, authentication weaknesses, insecure data handling, and potential client-side exploits like buffer overflows and injection attacks .BreachLock thick client application penetration testing assesses applications that operate on users devices and communicate with a server or backend system. During thick client penetration testing, we identify security weaknesses not .
scratch test definition science
Thick client penetration testing not only identifies problems but also provides helpful insights to address them effectively. Organizations must prioritize the security of their thick client applications to protect sensitive data and maintain business flow. By regularly assessing their applications and implementing solid security measures . Here’s a comprehensive methodology for thick client penetration testing: Thick Client Penetration Testing Methodology 1. Pre-Engagement Preparation. Pen testing thick client apps, in the end, guarantees a proactive and all-encompassing approach to cybersecurity. Eventually reducing the likelihood of data breaches and safeguarding user data and organizational assets. 70%. of thick client applications have at least one critical vulnerability. 90%.
scratch test device
Tip from Udemy course Mastering thick client application penetration testing by Srinivas. We can go in the folder of the app we are analyzing and open the command prompt from there. We can then run our app and put the output of the execution of our app in a log file using the following command: ourapp.exe > ourapp-logs.txt In the case of thick client penetration testing, most of the tasks are performed at the client end So it heavily depends on the client’s system resources like CPU, memory, RAM, etc. Ex like . Penetration Testing » Thick Client Pentest Lab Setup: DVTA » Penetration Testing. Thick Client Pentest Lab Setup: DVTA. January 1, 2021 by Raj. Thick client applications are not new and have been around for many years and can be still easily found within a variety of organizations. Thick clients are majorly used across organizations for their .
In this blog post we will delve into the process of testing Linux thick client application to identify and address potential security vulnerabilities, by exploring various testing techniques and tools. . Memory analysis is crucial in penetration testing thick client applications. It involves examining the contents of computer memory when the . Proxy unaware thick client: Do not natively include proxy settings so the user is required to make some changes in the system’s host file Thick Client Testing Methodology. Currently, there is no definite methodology when it comes to thick clients because there is no standard. There is an OWASP thick client top 10 but it is still in development. For thick client penetration testing, there are two key methods: Black-Box Testing: It is the testing approach where the testers initiate the test without any prior knowledge about the app’s configurations. They carry out the testing of all functionalities of the application without any access to design, operation, and backend processes. .Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and prioritize remediation efforts to mitigate cyber risks. Tell us. about your scope. Name
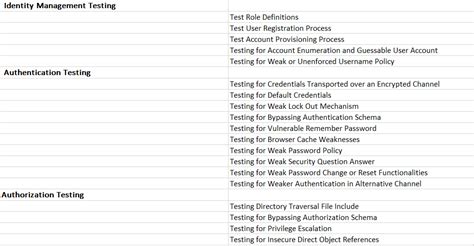
thick client pentest checklist
thick client penetration testing methodology
14 de set. de 2023 · Linux开关机. 在Linux下,我们常用 shutdown、reboot、poweroff、halt等进行关机或重启. 另外还有就是直接使用 init 修改循行等级进行,如:init 0、init 6等. 各命令的作用:. reboot 重启. 可接参数如下:. Reboot the system. --help Show this help --halt Halt the machine. -p --poweroff Switch off .
pen test on thick client|thick client pentest checklist